
CALLGOOSE

CALLGOOSE
BLOG
05 September 2024 | Tony Philip
5 Minute Read
In today's fast-paced digital landscape, security incidents can have a significant impact on business operations and data integrity. Therefore, reducing the Mean Time to Respond (MTTR) in your Security Operations Center (SOC) is crucial for effectively mitigating security threats and minimizing their impact. In this blog post, we'll explore strategies to improve MTTR and enhance the overall efficiency of your SOC.
Understanding MTTD and MTTR:
Mean Time to Detect (MTTD) refers to the time taken to detect a security incident from the moment it occurs. On the other hand, Mean Time to Respond (MTTR) measures the time taken to respond to and resolve the incident once it has been detected. Both MTTD and MTTR are critical metrics for evaluating the effectiveness of your SOC's incident response capabilities.
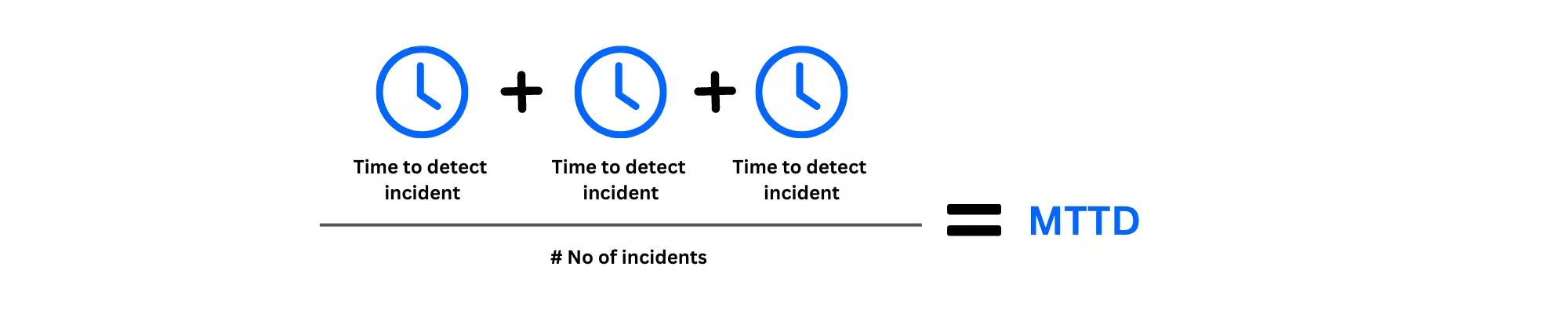
Improving MTTD:
Enhancing MTTR:
Reducing Mean Time to Respond (MTTR) in your Security Operations Center (SOC) is essential for effectively mitigating security threats and minimizing their impact on your organization. By implementing proactive monitoring, automated alerting, standardized incident response procedures, and continuous training initiatives, you can enhance your SOC's incident response capabilities and improve overall security posture. Investing in the right tools, technologies, and talent is key to achieving faster response times and ensuring optimal protection against evolving cyber threats.
By leveraging these tools and using Callgoose SQIBS Incident Management and Callgoose SQIBS Automation Platform , you can set up robust event-driven and Incident auto-remediation automation workflows to enhance efficiency, reliability, and responsiveness in your IT operations.
Callgoose SQIBS is a real-time Incident Management and Incident Response platform with an advanced On-Call schedule feature that keeps your organization more resilient, reliable, and always on. Callgoose SQIBS can seamlessly integrate with any software's or Tools including any AI to reduce alert noise , automate the workflows and improve the effectiveness of escalation policies for global teams. Several communication channels are supported, including Phone call, SMS, Mobile app push notifications, and many more.
Callgoose SQIBS has 'Automation Platform.' This feature offers Runbook Automation. Runbook automation plays a crucial role in enhancing incident response capabilities, enabling organizations to remediate incidents faster, minimize downtime, and ensure business continuity. By automating repetitive tasks, standardizing procedures, and enabling rapid execution of response actions, runbook automation empowers IT teams to respond swiftly and effectively to incidents, ultimately reducing the impact on business operations and enhancing overall resilience.

BLOG
5m Read

BLOG
5m Read
Enhanced IT Notifications for Global Teams Using Callgoose SQIBS Automation
20 February 2025
|
Tony Philip
Introduction In a globally distributed IT environment, ensuring that critical notifications reach the right teams at the right time is crucial for minimizing downtime and maintaining operational effic...

BLOG
5m Read
CALLGOOSE
SQIBS
Advanced Automation platform with effective On-Call schedule, real-time Incident Management and Incident Response capabilities that keep your organization more resilient, reliable, and always on
Callgoose SQIBS can Integrate with any applications or tools you use. It can be monitoring, ticketing, ITSM, log management, error tracking, ChatOps, collaboration tools or any applications
Callgoose providing the Plans with Unique features and advanced features for every business needs at the most affordable price.
Unique Features