
CALLGOOSE

CALLGOOSE
BLOG
05 September 2024 | Tony Philip
5 Minute Read
In today's interconnected digital landscape, businesses face a myriad of vulnerabilities, threats, and risks that can jeopardize their operations, integrity, and reputation. From cyberattacks and data breaches to regulatory compliance failures and operational disruptions, the impact of these threats can be severe and far-reaching.
In this blog, we'll delve into the concepts of vulnerabilities, threats, and risks, explore how they can affect business reputation, and discuss strategies for preventing reputational damage.
Understanding Vulnerabilities, Threats, and Risks:
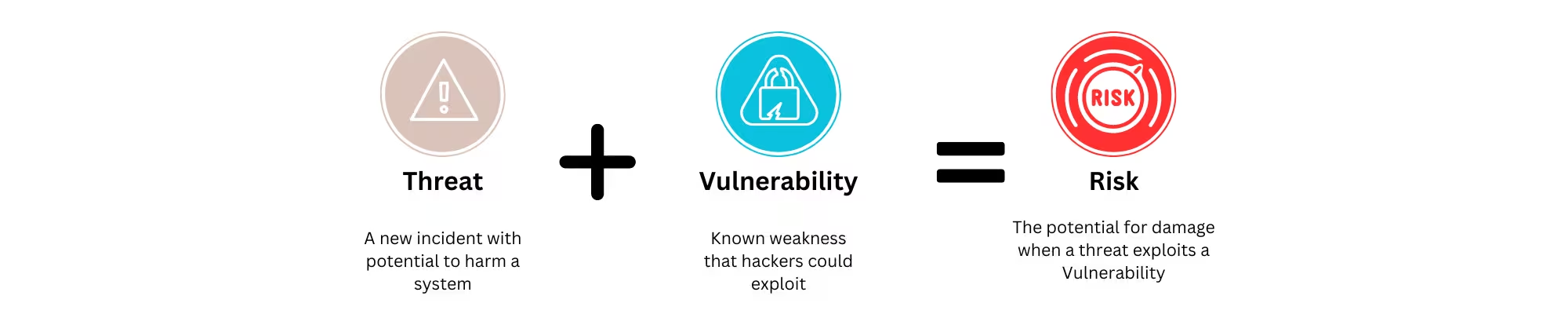
Impact of Vulnerabilities, Threats, and Risks on Business Reputation:
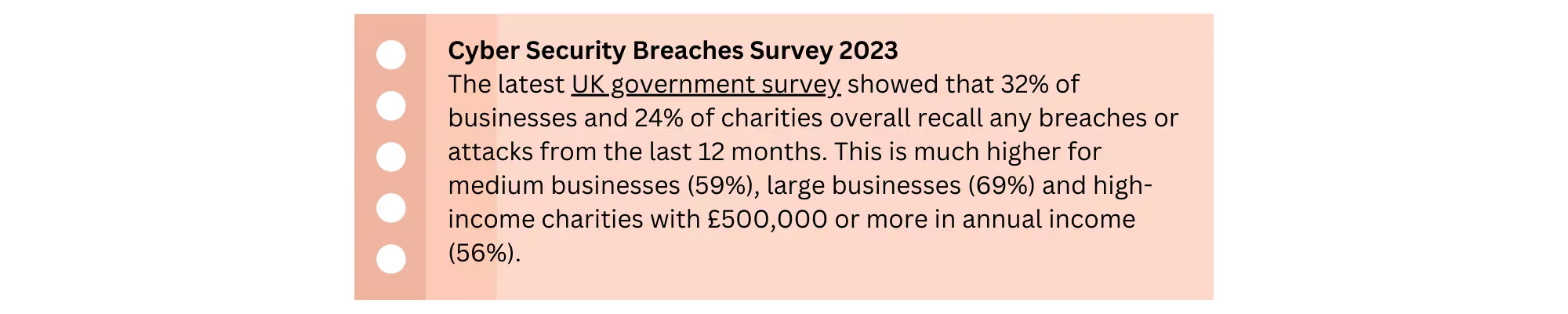
Preventing Reputational Damage:
Vulnerabilities, threats, and risks pose significant challenges to business reputation, integrity, and sustainability in today's digital age. By understanding the nature of these threats and implementing proactive measures to mitigate risks, organizations can safeguard their reputation, maintain customer trust, and thrive in a competitive landscape. By prioritizing security, compliance, transparency, and continuous improvement, businesses can prevent reputational damage and build resilience against emerging threats and challenges.
Learn how Callgoose SQIBS can help to reduce the Downtime for businesses by using effective Incident management and Incident response platform.
By using Callgoose SQIBS Automation Platform, you can set up robust Incident auto-remediation automation workflows and event-driven automation workflows to enhance efficiency, reliability, and responsiveness in your IT operations.
Refer Callgoose SQIBS Incident Management and Callgoose SQIBS Automation for more details
Callgoose SQIBS is an effective On-Call schedule and Incident Management and Response platform keep your organization more resilient, reliable, and always on. It can integrate with any software's or Tools including any AI to reduce alert noise , automate the workflows and improve the effectiveness of escalation policies for global teams. By Integrating Callgoose SQIBS into your environment can get immediate alerts on any kinds of Incidents due to Vulnerabilities, threats, and risks
BLOG
5m Read
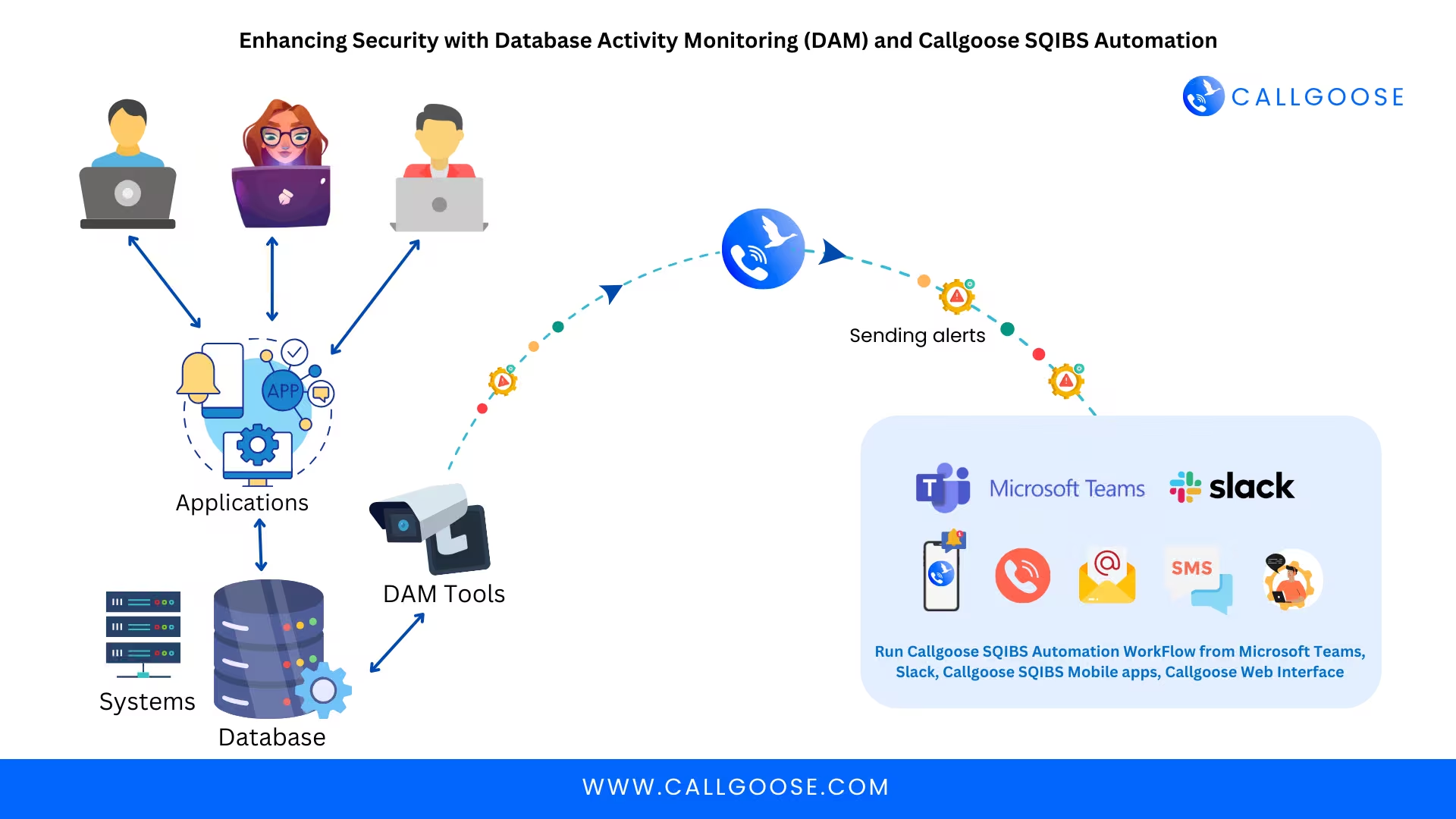
Enhancing Security with Database Activity Monitoring (DAM) and Callgoose SQIBS Automation
13 March 2025
|
Tony Philip
Introduction Data is the backbone of every business, and databases store critical information such as customer details, financial records, and intellectual property. However, with increasing cyber thr...

BLOG
5m Read
CALLGOOSE
SQIBS
Advanced Automation platform with effective On-Call schedule, real-time Incident Management and Incident Response capabilities that keep your organization more resilient, reliable, and always on
Callgoose SQIBS can Integrate with any applications or tools you use. It can be monitoring, ticketing, ITSM, log management, error tracking, ChatOps, collaboration tools or any applications
Callgoose providing the Plans with Unique features and advanced features for every business needs at the most affordable price.
Unique Features